
The first truly viral computer viruses were spread through floppy disks
The earliest computer viruses were pretty tame. In fact, the very earliest viruses — like “Creeper” which just displayed the message “I’M A CREEPER : CATCH ME IF YOU CAN” — were not only innocuous experiments in computing, but completely quarantined to their home networks, (Creeper was stuck on the TENEX operating system). This was in 1971, when there was no unified Internet.
Nowadays we’re used to fearing millions of viruses, all the time, and we’re used to them spreading through the Internet — either you download and run something sketchy from a P2P network, or you click a weird link in an email, and the next thing you know your system is completely compromised. When everything is connected to everything, contagions can spread easily. Virus protection is big business, too — consumers spend billions of dollars a year on it.
It turns out that this nightmare had a very slow start, and an earlier one than you might expect. The first viruses to spread outside of private networks did so entirely offline, back when the Internet was still young and tiny. These first, really “viral” viruses were floppy disk based, and carried from computer to computer by human hands.
How exactly did the first viruses to spread in the “wild” work? And who invented them? Well, it depends on who you ask, and whether they’re a Mac or a PC. The first Apple virus was a teenager’s prank; the first PC virus was a corporate anti-piracy measure.
Elk Cloner

Elk Cloner: The program with a personality (not an actual screen shot)
In 1981, Richard Skrenta was in 9th grade and a force to be reckoned with. He was mischievous, very, very clever, and armed with an Apple II. One of his favorite things to do with it was write code to prank his friends’ pirated computer games. From an interview with Skrenta in 2000:
“I had been playing jokes on schoolmates by altering copies of pirated games to self-destruct after a number of plays. I’d give out a new game, they’d get hooked, but then the game would stop working with a snickering comment from me on the screen (9th grade humor at work here).”
Eventually Skrenta’s friends stopped letting him touch their floppy disks — they stopped lending him games, they stopped playing games he had pirated, etc. But Skrenta was a determined prankster, and Apple was a very different company back then, one that welcomed tinkerers of all stripes. The Apple II was much closer to a Raspberry Pi than a Macbook Pro. Skrenta pored over technology books, looking for holes in the Apple II’s system. Eventually, he worked out a way to insert code that would execute, onto games, without ever touching the disks himself:
“I hit on the idea to leave a residue in the operating system of the school’s Apple II. The next user who came by, if they didn’t do a clean reboot with their own disk, could then be touched by the code I left behind.”
He took two weeks to write this “residue,” in assembly language. He called the program Elk Cloner. Elk Cloner was what is known as a “boot sector” virus. This is how it spread: when an uninfected disk was inserted into an infected computer (the school computer), the computer infected the floppy disk, i.e. it made a copy of Elk Cloner in the floppy disk’s boot sector — code that runs automatically on boot. When a student brought any infected floppy disk (and Skrenta seeded many) to another computer, and booted the computer with the infected floppy disk inside, the computer was infected with a copy of Elk Cloner.
The virus caused subtle errors, until the 50th time you inserted the disk into a computer. Then, instead of your game starting, the following poem came on the screen:
“Elk Cloner: The program with a personality
It will get on all your disks
It will infiltrate your chips
Yes, it’s Cloner!
It will stick to you like glue
It will modify RAM too
Send in the Cloner!”
This timed-release was to let the program go undetected for longer, thus give it a better chance of spreading — by the time a user saw this message, they could have already spread Elk Cloner to hundreds of disks and computers, and they would be seeing the message everywhere, for weeks and weeks. “Rather than blowing up quickly,” Skrenta said in an interview, “to the extent that it laid low it could spread beyond the first person to others as well.”
Spread it did. In a scene right out of a movie, Elk Cloner ended up on Skrenta’s math teacher’s graphing software. The teacher was very upset and, suspecting Skrenta, accused him of breaking into his office. His cousins in Baltimore caught it (Skrenta lived in Pittsburgh), and, years later, he discovered that a sailor in the US Navy had, too. Scientific American mentioned it, a few years later, when the relatively benign Elk Cloner had been replaced by a host of much more malignant viruses.
Brain
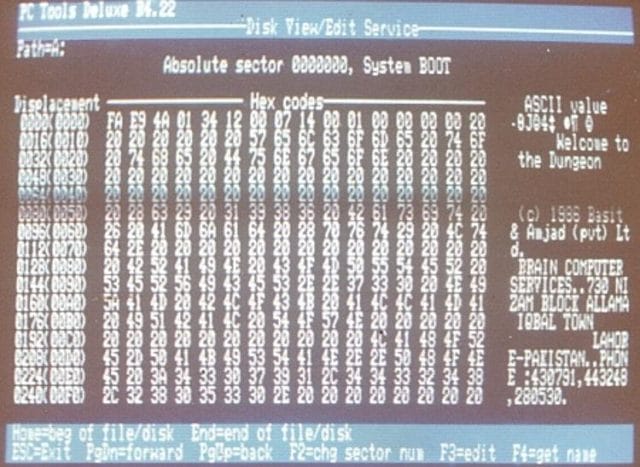
The first widespread virus for an IBM PC operating system was called Brain. Like Elk Cloner, it was also a boot sector virus, although its creators had little in common with Skrenta. Pakistani brothers Basit and Amjad Farooq Alvi say they had’t heard of him or Elk Cloner when they wrote Brain in 1986. Basit was 17 and Amjad was 24 at the time.
The founders of Brain Computer Services, the Alvi brothers say they developed the Brain virus to punish and track piracy of their medical software for the IBM PC. If the disk the program was on was bootlegged, the boot sector was replaced with an infected boot sector, squatting on precious kilobytes of memory, slowing down the disk and sometimes preventing the user from saving. Like Elk Cloner, it was mostly a harmless annoyance, and it didn’t destroy any data. But the infected boot sector also included an ominous message:
“Welcome to the Dungeon (c) 1986 Basit & Amjad (pvt) Ltd. BRAIN COMPUTER SERVICES 730 NIZAB BLOCK ALLAMA IQBAL TOWN LAHORE-PAKISTAN PHONE :430791,443248,280530. Beware of this VIRUS…. Contact us for vaccination………… $#@%$@!!”
The contact information in the message was real. The idea was to track replicated disks. Whenever the brothers received a call, visit, or letter from someone, spooked by the warning, seeking “vaccination,” they’d be able to identify and locate another pirated instance of their software. “By putting [that] code in,” Amjad said in an interview with F-Secure in 2012, “we [could] see and watch whether it [would] spread all over the world or remain within a certain group of people.” The virus also kept count of how many times the disk had been replicated.
What they discovered was piracy was widespread, and bootlegged versions of their software were travelling far. Very far. “The first call we received was from Miami USA,” Amjad said. “[The caller] was having trouble with the floppy and she discovered [an] extra piece of code inside.”

The Alvis’ F-Secure interview, in 2011
It was the first call of many, and many from the United States. One problem was that it seemed that Brain was transmissible to different floppy disks — much like Elk Cloner — even ones that weren’t direct copies of their medical software. The University of Delaware experienced a kind of Brain epidemic in 1986, and then it began popping up in a million other places. Though there was never any legal action, there was a lot of media coverage. The Brain and its creators were even written-up in Time Magazine in 1988.
“A rogue computer program introduced into personal computers at The Providence Journal-Bulletin earlier this month destroyed one reporter’s files and spread to floppy disks throughout the newspaper’s computer system,” the New York Times reported. “Computer specialists believe this is the first time an American newspaper’s computer system has become contaminated with such a rogue program, known as a computer ‘virus.’”
The Alvis ended up having to change their phone numbers, and removed their contact information entirely from later instances of the virus. They say they stopped selling contaminated software in 1987. Their company grew into a telecommunications company, and is now the largest Internet service provider in Pakistan. It’s still located at the same address in Lahore.
And Now, Chaos

Skrenta on TechCrunch in 2012
As for Skrenta, who invented Elk Cloner, he worked in Internet security for a while through the 1990s. Now he’s the CEO of a search company, Blekko, which raised $60.2 million.
Though floppy disks aren’t really in the picture anymore, boot sector viruses still exist. When they are transmitted it’s usually off of a USB. But people are using hardware to transfer their files less and less, and experts say the boot sector virus’ days may finally be coming to an end.
Which, of course, doesn’t mean the war is over. It’s bigger than ever, it’s just mostly online. “The anti-virus industry makes me sad,” Skrenta told The Register. “We should build systems to be more resistant to computer viruses rather than have a multi-million dollar industry to do clean up.”
Neither he nor the Alvis feel a sense of guilt for having caused the first few sparks of the hellish inferno that is today’s viral landscape. “The only consolation is that the genie would have gotten out anyway,” he wrote on his blog. “But it’s fun to be the first to let it out. :-)”
This post was written by Rosie Cima; you can follow her on Twitter here. To get occasional notifications when we write blog posts, please sign up for our email list



